What is Ransomware?
Ransomware is a kind of intelligent malware, but unlike other malware that merely corrupt, delete files or does some other suspicious behavior, this malware locks your system, files and apps, and demands money from you, if you want to get them back. I said intelligent because this malware helps directly the attacker to earn money. Other kinds of malwares, like viruses, trojan horses etc, merely corrupt the system or steal some sensitive data, but rarely result in some monetary benefit to the attacker (unless the malware steals some sensitive information like credit card numbers etc). Image via PCWorld.com
The Origin of Ransomware
Initially, ransomware were largely popular in Russia, infecting thousands of computer systems and spreading like wildfire. These kind of malware are harder to detect, as they can come as harmless small programs attached to software freely available over the interwebs. Most of them can enter your system through files of already infected system, email attachments or from already existing malware. Once the ransomware has found its host, it begins to attack by locking user access to files, folders, system settings or apps. Upon trying to open those files and programs, the user gets the message that they have been blocked and cannot be opened unless the user agrees to pay an amount. Usually, there is also a way to contact the attackers who may be sitting in some other part of the world, directly taken control of your system.
Types of Ransomware
Ransomwares are normally classified into two types, encrypting ransomware and non-encrypting ransomware. Encrypting ransomware are those who encrypt the files, programs etc of your system and demand a ransom to un-encrypt them. Usually encryption is done using a strong hashing algorithm that can take several thousands of years for a normal desktop PC to break them. So the only way that the user gets back his files is by giving the ransom amount and obtaining the unlock key. This is the most harmful ransomware for its sheer attacking mechanism. Another type of ransomware is the non-encrypting one. This one doesn’t encrypt your files, but rather blocks access to them and shows irritating messages when you try to access them. This is a less harmful ransomware and the user can easily get rid of them by taking backup of important files and installing the operating system again.
Examples of Ransomware Attacks
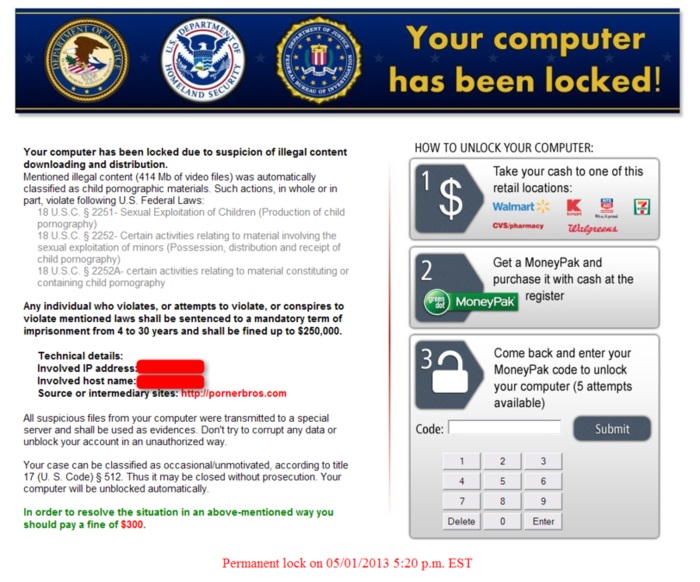
One of the recent ransomware that caused the most harm was in 2013, is known as CryptoLocker. The brain behind this malware was a Russian hacker by the name of Evgeniy Bogache. The malware, when injected into a host system, scans the hard drive of the victim and targets specific file extensions and encrypts them. These could be important files or programs that user really needs, like documents, programs or keys. The encryption is done using a 2048-bit RSA key pair, with the private key uploaded to command and control server. The programs then threatens the user that it will delete the private key, unless a payment in form of bitcoins is done within three days. A 2048 RSA key is indeed a big protection, and it will take a normal desktop PC several thousands of years to break the key using brute force. The user, helpless agrees to pay the amount in order to get the files back. It is estimated that this CryptoLocker Ransomware procured at least $3 million before it was shut down. While thats a lot of money, another ransomware by the name of WinLock was able to procure $16 million in ransom. While it did not encrypt the system like CryptoLocker, what it did was to restrict the app access of the user and show pornographic images instead. The user was then forced to send a premium rate SMS, costing around $10 to get a code to unlock the ransomware. All these attacks were way back in 2013. However, the most recent attack was by an updated form of ransomware, called CryptoWall 2.0. According to a New York Times report this ransomware attacked PCs in a fashion similar to CryptoLocker, and attacked specially important files in victim’s system, like tax receipts, bills etc. Then it demanded a ransom of $500. The price of the ransom doubled after a week, and further a week later, the unlock key was deleted. Recently according to some reports, CryptoWall has been updated to version 3.0, and apparently it has become more dangerous than ever. This version of CryptoWall encrypts the user files by a system of intelligent scanning, and then generates a unique link for the user. As a protection to preserve anonymity of the attackers and make government agencies harder to arrest them, this ransomware is not only using Tor, but also I2P which makes it really hard to track them. While it may sound ironic, but CrytoWall has really good customer service. As they have to maintain a reputation to get more and more money, they provide decryption keys to the user as quickly as possible, often within hours after the ransom has been paid out. Another grave incident of ransomware happened when an autistic student hanged himself after receiving a ransomware e-mail. According to this report, the teen received a fake email from police saying that he has been caught browsing illegal websites and needed to pay a hundred pounds or face prosecution. The teen, panicked and hanged himself, unable to face the tragedy. While these types of emails are common, one needs to make sure that one should not trust them no matter how official looking they are. Often they lead the user to phishing websites where the attacker gets hold to the users’ bank accounts and other important passwords. The rule of the thumb is bank agencies and law enforcement agencies will never ask for private credentials or payments via the Internet. So if you receive such emails, there is a good chance that they are hoax. You can always call up by getting their official number to know if they have indeed given you such notice. FBI Ransomware Screenshot Ransomware is a good bet for black hats because there is usually a lot of money that can be got just by creating small programs that lock or encrypt your system in some way. While mostly popular in Windows platform, some other OSes like OS X also get affected by ransomware, like one in July 2013 that blocked the user’s browser and accuses him of downloading pornography. Several reports suggests than ransomware attacks are increasing day by day. They are mostly spread by spam emails, often coming as attachments. Internet users really need to be careful while browsing unofficial websites and opening such emails.
Why is it hard to catch Ransomware hackers?
Most of the ransomware originates from post-soviet countries like Russia. While these people do demand ransom, but the payment is in form of bitcoins, a decentralized crypto-currency known for its anonymity and not leaving any traces. Also, the hackers being of foreign origin, diplomatically its hard to convince foreign governments to take action on them.
How do we protect ourselves against Ransomware?
As the old saying goes, prevention is better than cure. So how does one protect himself from ransomware? Well the easiest way would be to have a antivirus or anti-malware installed in one’s system and always keep it updated. While free antiviruses are quite good, one must not hesitate to get a paid one for better protection. Apart from that, make sure you do not download suspicious programs off the Internet. While downloading programs, always download from the official sites and not from 3rd party untrusty ones. And remember always, keep a backup of all important files. With so may set it and forget it backup programs available, its really easy and hassle free to have a backup program. You can also upload or sync the files on Google Drive/Dropbox etc, so that not only you have a backup, but also you can access those files from no matter where you are. Remember, a stitch in time, saves nine. Better safe than sorry.
How to remove Ransomware malware?
Earlier, the only way to get rid of encrypting ransomware malware was to either pay the attackers or accept that the files have been lost forever. However, currently some computer security researchers have come up with programs which will allow users to uncrypt their hard drives files without paying a ransom. Like this website, it allows users to upload an non-sensitive encrypted file on their site and enter an email address. Upon successful decryption, the site will email you the private key along with instructions how to remove cryptolocker from your hard drive. The program was developed by FireEye and FoxIT, and used methods of reverse engineering to break CryptoLocker. As the rule follows, every encrypted thing can be decrypted, it just takes time. It seems the good forces of computer science are not losing afterall. SEE ALSO: Top 10 Antivirus Apps For Android Smartphones